RIPng — RIP and IPv6
RIP next generation, or RIPng, is the version of RIP that supports IPv6.
This is an example of a typical small network configuration using RIPng routing.
Your internal R&D network is working on a project for a large international telecom company that uses IPv6. For this reason, you have to run IPv6 on your internal network and you have decided to use only IPv6 addresses.
Your network has two FortiGate units running the RIPng dynamic routing protocol. Both FortiGate units are connected to the ISP router and the internal network. This configuration provides some redundancy for the R&D internal network enabling it to reach the internet at all times.
This section includes the following topics:
- Network layout and assumptions
- Configuring the FortiGate units system information
- Configuring RIPng on FortiGate units
- Configuring other network devices
- Testing the configuration
- Debugging IPv6 on RIPng
Network layout and assumptions
Basic network layout
Your internal R&D network is working on a project for a large international telecom company that uses IPv6. For this reason, you have to run IPv6 on your internal network and you have decided to use only IPv6 addresses.
Your network has two FortiGate units running the RIPng dynamic routing protocol. Both FortiGate units are connected to the ISP router and the internal network. This configuration provides some redundancy for the R&D internal network enabling it to reach the internet at all times.
All internal computers use RIP routing, so no static routing is required. And all internal computers use IPv6 addresses.
Where possible in this example, the default values will be used or the most general settings. This is intended to provide an easier configuration that will require less troubleshooting.
In this example the routers, networks, interfaces used, and IP addresses are as follows:
Rip example network topology
| Network | Router | Interface & Alias | IPv6 address |
|---|---|---|---|
| R&D | Router1 | port1 (internal) | 2002:A0B:6565:0:0:0:0:0 |
| port2 (ISP) | 2002:AC14:7865:0:0:0:0:0 | ||
| Router2 | port1 (internal) | 2002:A0B:6566:0:0:0:0:0 | |
| port2 (ISP) | 2002:AC14:7866:0:0:0:0:0 |
Network topology for the IPv6 RIPng example
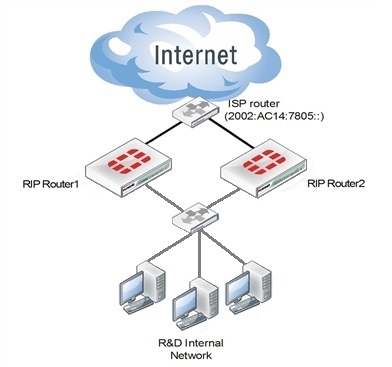
Assumptions
The following assumptions have been made concerning this example:
- All FortiGate units have 5.0+ firmware, and are running factory default settings.
- All CLI and web-based manager navigation assumes the unit is running in NAT/Route operating mode, with VDOMs disabled.
- All FortiGate units have interfaces labelled port1 and port2 as required.
- All firewalls have been configured for each FortiGate unit to allow the required traffic to flow across interfaces.
- All network devices are support IPv6 and are running RIPng.
Configuring the FortiGate units system information
Each FortiGate unit needs IPv6 enabled, a new hostname, and interfaces configured.
To configure system information on Router1 - web-based manager:
- Go to System > Dashboard > Status.
- For Host name, select Change.
- Enter “Router1”.
- Go to System > Config > Features.
- Enable IPv6 and click Apply.
- Go to System > Network > Interfaces.
- Edit port1 (internal) interface.
- Set the following information, and select OK.
| Alias | internal |
| IP/Netmask | 2002:A0B:6565::/0 |
| Administrative Access | HTTPS SSH PING |
| Description | Internal RnD network |
| Administrative Status | Up |
- Edit port2 (ISP) interface.
- Set the following information, and select OK.
| Alias | ISP |
| IP/Netmask | 2002:AC14:7865::/0 |
| Administrative Access | HTTPS SSH PING |
| Description | ISP and internet |
| Administrative Status | Up |
To configure system information on Router1 - CLI:
config system global
set hostname Router1
set gui-ipv6 enable
end
config system interface
edit port1
set alias internal
set allowaccess https ping ssh
set description "Internal RnD network"
config ipv6
set ip6-address 2002:a0b:6565::/0
end
next
edit port2
set alias ISP
set allowaccess https ping ssh
set description "ISP and internet"
config ipv6
set ip6-address 2002:AC14:7865::
end
end
To configure system information on Router2 - web-based manager:
- Go to System > Dashboard > Status.
- For Host name, select Change.
- Enter “Router2”.
- Go to System > Config > Features.
- Enable IPv6 and click Apply.
- Go to System > Network > Interfaces.
- Edit port1 (internal) interface.
- Set the following information, and select OK.
| Alias | internal |
| IP/Netmask | 2002:A0B:6566::/0 |
| Administrative Access | HTTPS SSH PING |
| Description | Internal RnD network |
| Administrative Status | Up |
- Edit port2 (ISP) interface.
- Set the following information, and select OK.
| Alias | ISP |
| IP/Netmask | 2002:AC14:7866::/0 |
| Administrative Access | HTTPS SSH PING |
| Description | ISP and internet |
| Administrative Status | Up |
To configure system information on Router2 - CLI:
config system global
set hostname Router2
set gui-ipv6 enable
end
config system interface
edit port1
set alias internal
set allowaccess https ping ssh
set description "Internal RnD network"
config ipv6
set ip6-address 2002:a0b:6566::/0
end
next
edit port2
set alias ISP
set allowaccess https ping ssh
set description "ISP and internet"
config ipv6
set ip6-address 2002:AC14:7866::
end
end
Configuring RIPng on FortiGate units
Now that the interfaces are configured, you can configure RIPng on the FortiGate units.
There are only two networks and two interfaces to include — the internal network, and the ISP network. There is no redistribution, and no authentication. In RIPng there is no specific command to include a subnet in the RIP broadcasts. There is also no information required for the interfaces beyond including their name.
As this is a CLI only configuration, configure the ISP router and the other FortiGate unit as neighbors. This was not part of the previous example as this feature is not offered in the web-based manager. Declaring neighbors in the configuration like this will reduce the discovery traffic when the routers start up.
Since RIPng is not supported in the web-based manager, this section will only be entered in the CLI.
To configure RIPng on Router1 - CLI:
config router ripng
config interface
edit port1
next
edit port2
end
config neighbor
edit 1
set interface port1
set ipv6 2002:a0b:6566::/0
next
edit 2
set interface port2
set ipv6 2002:AC14:7805::/0
end
To configure RIPng on Router2 - CLI:
config router ripng
config interface
edit port1
next
edit port2
end
config neighbor
edit 1
set interface port1
set ipv6 2002:a0b:6565::/0
next
edit 2
set interface port2
set ipv6 2002:AC14:7805::/0
end
Configuring other network devices
The other devices on the internal network all support IPv6, and are running RIPng where applicable. They only need to know the internal interface network addresses of the FortiGate units.
The ISP routers need to know the FortiGate unit information such as IPv6 addresses.
Testing the configuration
In addition to normal testing of your network configuration, you must also test the IPv6 part of this example.
For troubleshooting problems with your network, see the FortiOS Handbook Troubleshooting chapter.
Testing the IPv6 RIPng information
There are some commands to use when checking that your RIPng information is correct on your network. These are useful to check on your RIPng FortiGate units on your network. Comparing the output between devices will help you understand your network better, and also track down any problems.
diagnose ipv6 address list
View the local scope IPv6 addresses used as next-hops by RIPng on the FortiGate unit.
diagnose ipv6 route list
View ipv6 addresses that are installed in the routing table.
get router info6 routing-table
View the routing table. This information is almost the same as the previous command (diagnose ipv6 route list) however it is presented in an easier to read format.
get router info6 rip interface external
View brief output on the RIP information for the interface listed. The information includes if the interface is up or down, what routing protocol is being used, and whether passive interface or split horizon are enabled.
get router info6 neighbor-cache list
View the IPv6/MAC address mapping. This also displays the interface index and name associated with the address.
Debugging IPv6 on RIPng
The debug commands are very useful to see what is happening on the network at the packet level. There are a few changes to debugging the packet flow when debugging IPv6.
The following CLI commands specify both IPv6 and RIP, so only RIPng packets will be reported. The output from these commands will show you the RIPng traffic on your FortiGate unit including RECV, SEND, and UPDATE actions.
The addresses are in IPv6 format.
diagnose debug enable
diagnose ipv6 router rip level info
diagnose ipv6 router rip all enable
These three commands will:
Turn on debugging in general
Set the debug level to information, a verbose reporting level
Turn on all RIP router settings
Part of the information displayed from the debugging is the metric (hop count). If the metric is 16, then that destination is unreachable since the maximum hop count is 15.
In general, you should see an update announcement, followed by the routing table being sent out, and a received reply in response.

